Background & Engineering Issues
Software architectures such as CBSD, SOA and microservices drive the advancement of software engineering, while software technologies such as CI/CD, DevOps and containerization increase the efficiency of software development.
However, existing architectures and code collaboration methods have the following drawbacks.
(1) Insecure centralized management. Existing methods rely on trusted third parties (TTP) to centrally manage data and server resources. However, if TTP experiences system crashes or internal corruption, all data or resources involved in software collaboration would be at security risk.
(2) Unreliable communication. Without reliable safeguards, the cross-team communication process is vulnerable to malicious attacks, resulting in the loss or corruption of exchanged information and subsequently reducing the credibility of information.
(3) Leakage of privacy data. Source code can be read arbitrarily from the shared mainline during processes of integration and deployment. This indicates a lack of emphasis on protecting original copyrights.
(4) Unavailable system/service. Existing methodologies fail to identify and clear unavailable systems or services immediately, wasting a lot of computing resources.
Contributions
1
We propose a decentralized storage network infrastructure with a blockchain and an off-chain file storage system, which can support trustworthy transaction processing by using a built-in consensus mechanism.
3
A cross-node communication protocol is designed, aiming to guarantee the reliability and integrity of messages during the cross-team communication process.
2
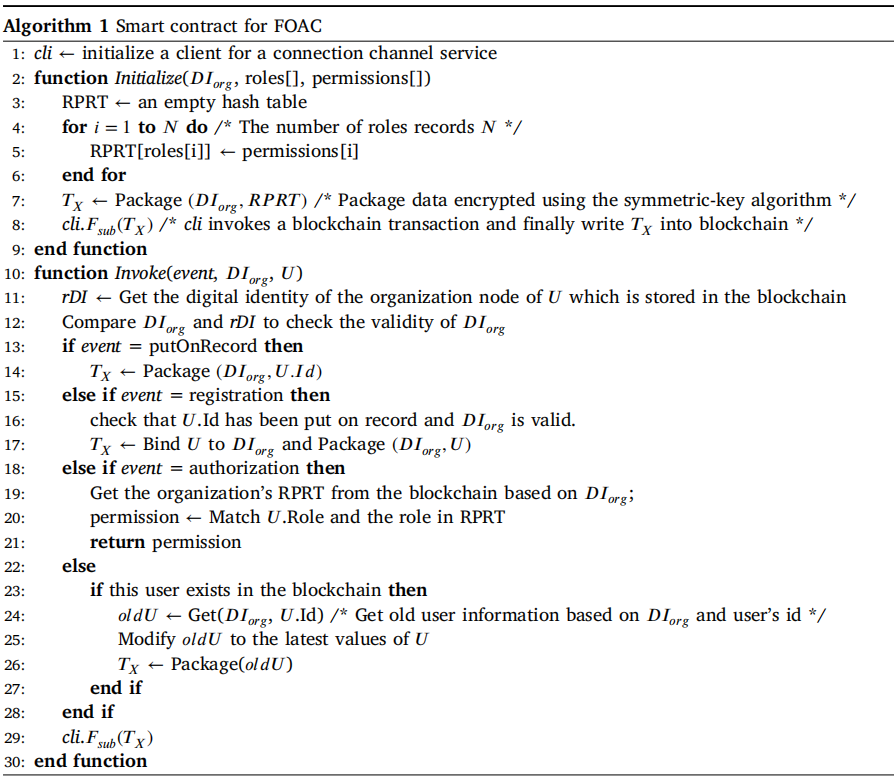
Three smart contracts are designed to realize reusable but invisible code collaboration, including decentralized access control, establishment and verification of code copyrights, and generation and supervision of containers.
4
We implement communication a prototype process. system to evaluate the model security and performance, and verify that our model can resist common attacks and have significant advantages compared to existing solutions.
Problem Formulation
Attacker model
Single point of failure. Any single component of the system can be subject to mistakes or malicious attacks.
Collusion attacks. Two or more malicious entities collaborate to conduct an attack or breach together.
Man-in-the-middle attacks. The attacker attempts to insert himself as an intermediary between two communicating parties in order to steal, tamper with or interfere with the communication data stream.
Replay attacks. To spoof the system, the attacker sends data packets that have already been received by the destination host.
Sybil attacks. A small number of nodes in a peer-to-peer network control multiple fake identities and then use these identities to control or influence a large number of normal nodes in the network.
Blockify attacks. The attacker tries to access the private blockchain, get the current block, and then change or delete the block information.
Design goals
Mutual authentication. To ensure that the identities of participants in code collaboration are trustworthy, we use blockchain to verify digital identities and organizations. Only authorized users can participate in code component collaboration.
Autonomy. The process of generating code copyrights and containers is controlled by smart contracts instead of relying on TTP.
Privacy protection. The workflow of our model cannot leak privacy code. We ensure that privacy data is encrypted during collaboration process.
Traceability. Privacy data and transaction records are stored in the blockchain for tracing the history.
Integrity. Ensure that the integrity of messages transmitted by nodes can be checked and verified.
Proposed Model
—— Overview
The proposed model is divided into four parts. First, four modules are designed to achieve the goal of code collaboration and reusable but invisible right management. Then, there are three smart contracts and a consensus mechanism. Next, a cross-node communication protocol is designed to secure data exchanges.
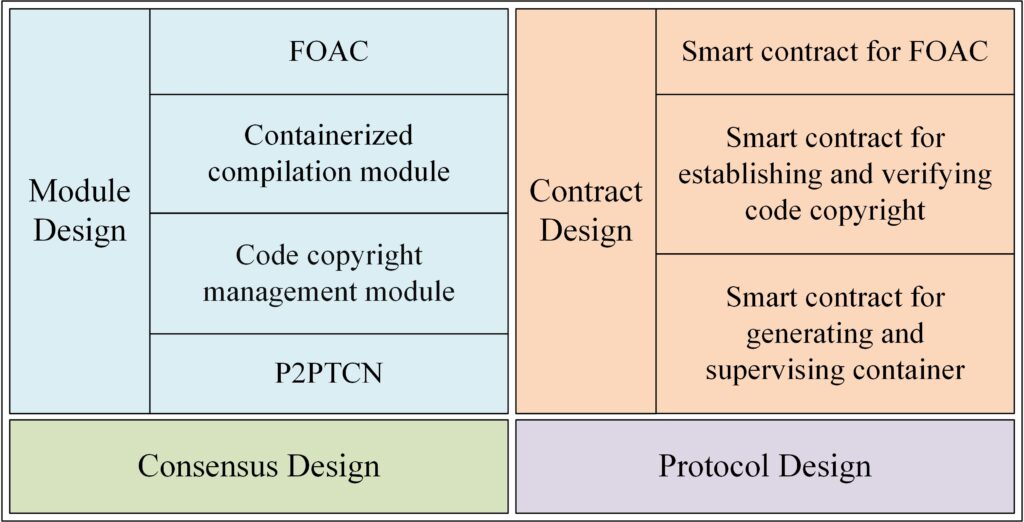
Details of module design are shown in the following figure.
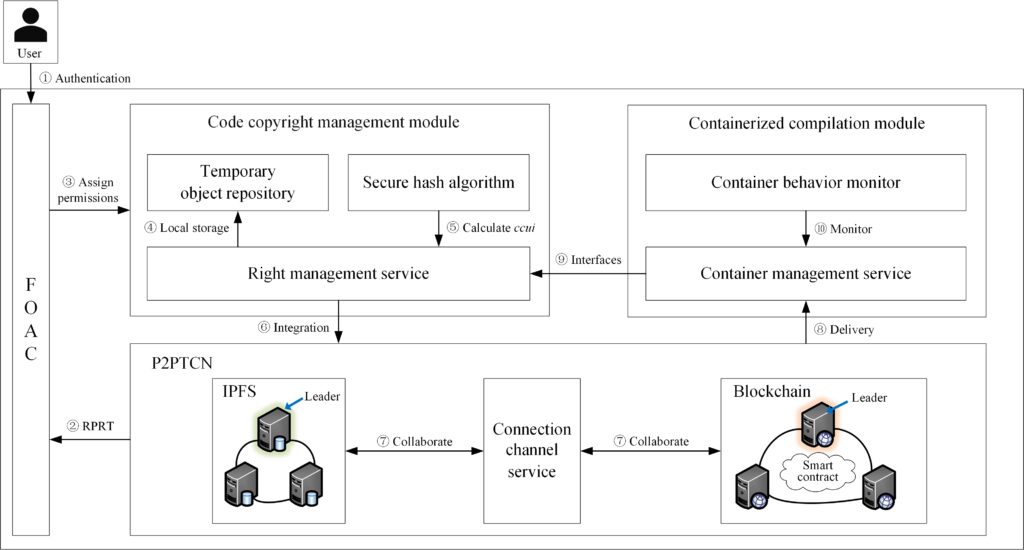
P2PTCN design
P2PTCN (peer-to-peer trusted collaboration network) is based on blockchain, IPFS and smart contracts, providing a trusted computing network and storage management service for other modules.
FOAC design
FOAC (filing-oriented access control model) is a decentralized access control technology, providing mutual authentication.
Code copyright management module design
The code copyright management module supports code integration and privacy protection, including task allocation and collaboration for code components, version control of privacy code component and code copyright management.
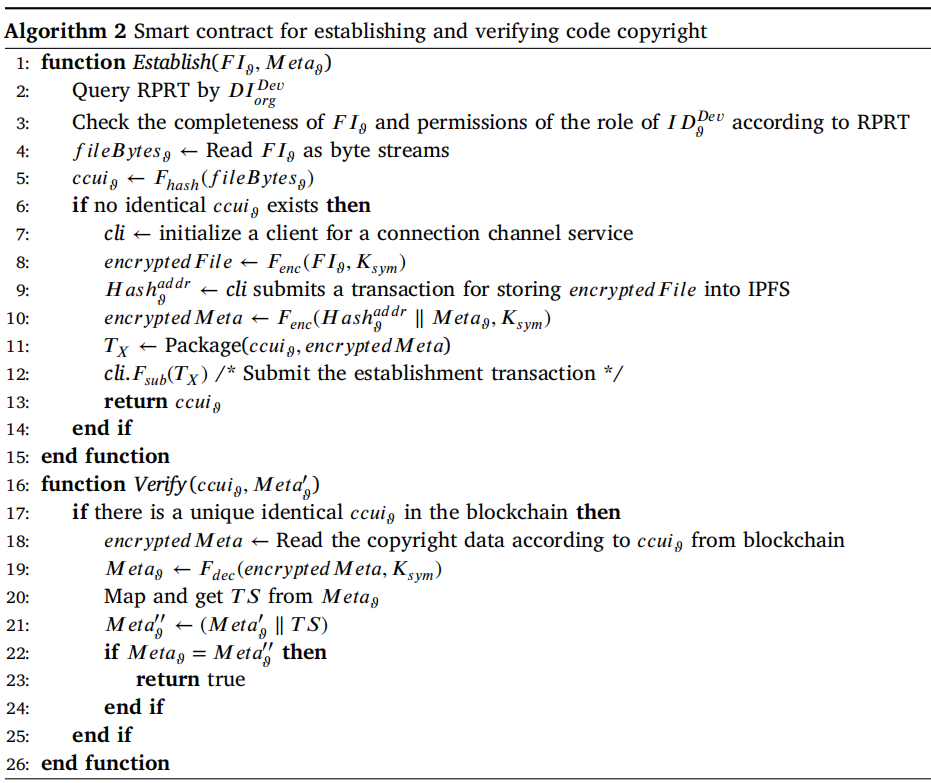
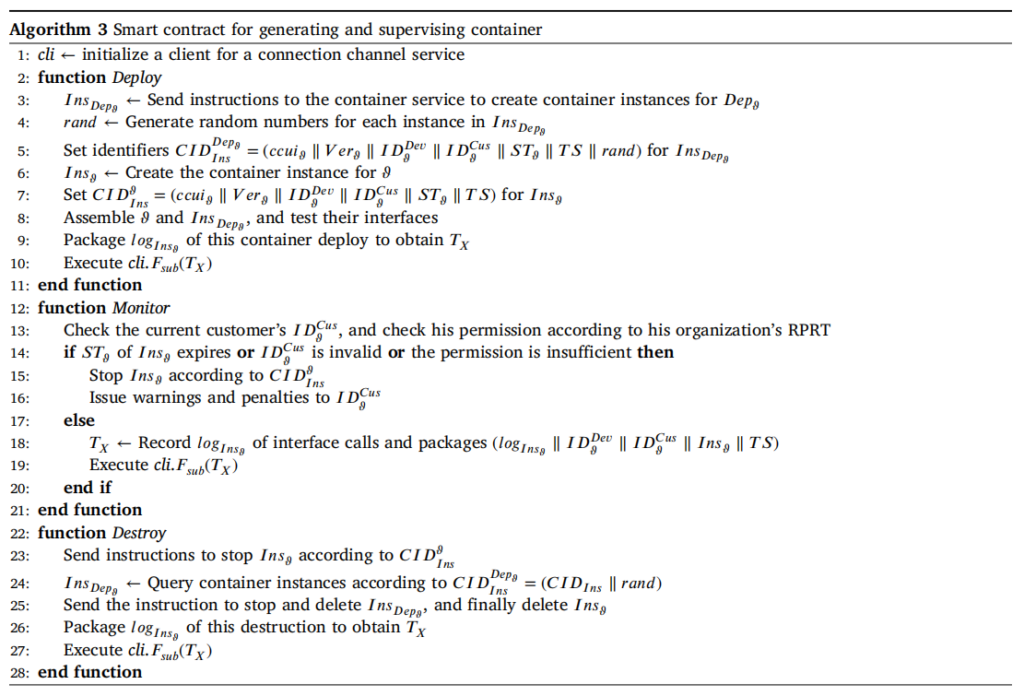
Containerized compilation module design
The containerized compilation module can automate the creation of containers from code components. The module can also credibly supervise container instances without relying on TTP, thus protecting the privacy of container data.
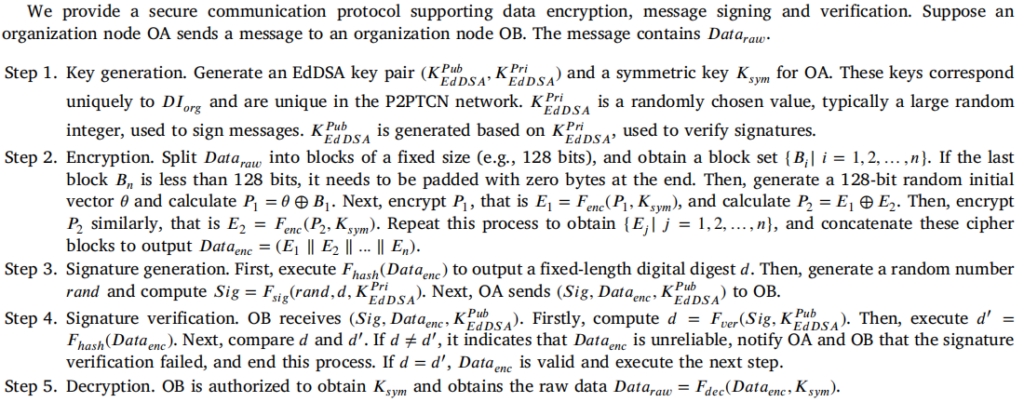
Information communication protocol design
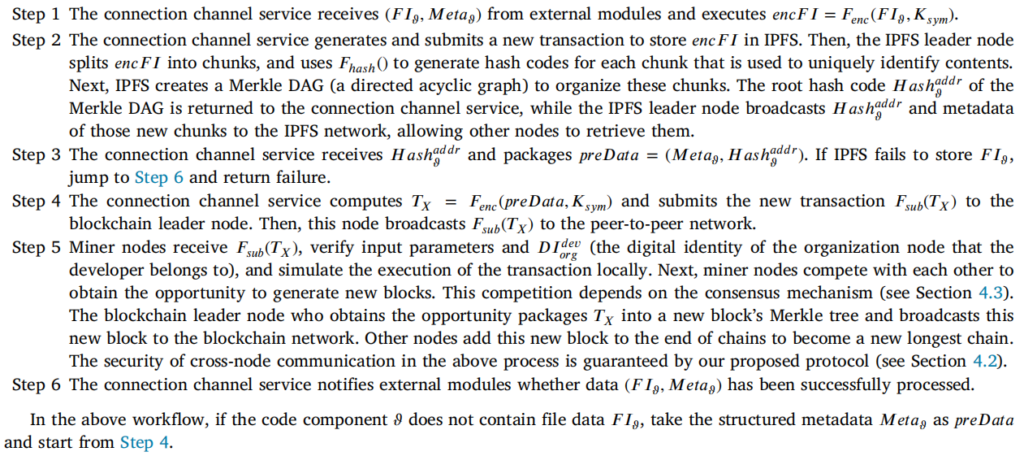
For question: Since we assume attackers exist in the distributed collaborative environment, how do we determine that messages or data transmitted between nodes in P2PTCN are complete and have not been tampered with? How do we ensure that even if information is intercepted during transmission, attackers cannot obtain any useful data?
Consensus design
For question: How to ensure mutual trust and data consistency between blockchain nodes in P2PTCN?
We introduce a consensus mechanism which is based on RAFT. For details, please refer to the paper.
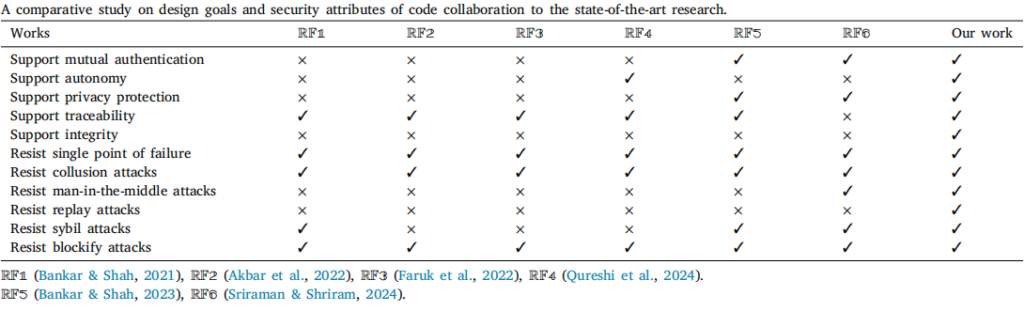
Model Validation & Analysis
Here, we only provide comparative results to demonstrate the advantages of our model. For details, please refer to the paper.

Limitations
Decentralized storage and management of the model relies heavily on blockchain and IPFS. With the growth of blockchain network scale, the time and computational resources required for consensus and data verification will increase significantly, potentially impacting the scalability and performance of the model in large-scale projects.
Next, although our model improves security through encryption and decentralized management, the additional layers of encryption, signature verification and consensus mechanisms may result in extra latency. This overhead may affect real-time collaboration, especially when many distributed nodes are involved in the workflow.
LINK
Source code: https://github.com/kcisgroup/2025WangWei